SECURE ACCESS SERVICE
EDGE (SASE)
Secure Access Service Edge
(SASE)
Supports enterprise’s hybrid work strategies with network security Goip Managed SASE Service helps streamline trusted real-time user authentication and access via a unified and cloud-based SASE platform, and provide real-time security and visibility to every user-device-application interaction.
This provides peace of mind for enterprises transferring key business applications to cloud operations so employees can access business systems remotely.
Win customers with quality and achieve brand with service
A “cloud” with centralized security control + a “network” for global office acceleration + a “side” with integrated security capabilities
Centralised Management Platform
This is a unified platform that enables enterprises to have network security deployment, settings and maintenance in a faster and simpler way.
High Flexibility & Scalability
The service allows the seamless integration of additional cybersecurity capabilities into the cloud-based framework, users, devices and applications can also be extended according to business needs.
Tailored Service Agreements
Maximises business agility with industry-leading Service Level Agreements (SLAs) tailored to the specific operational needs of different vertical industries.
Wide Global Coverage
Enables you to flexibly build secure access to cloud applications, websites and company data in different locations through more than 100 service access points across 76 countries and regions around the world.
SASE: Integrated Global Office Security
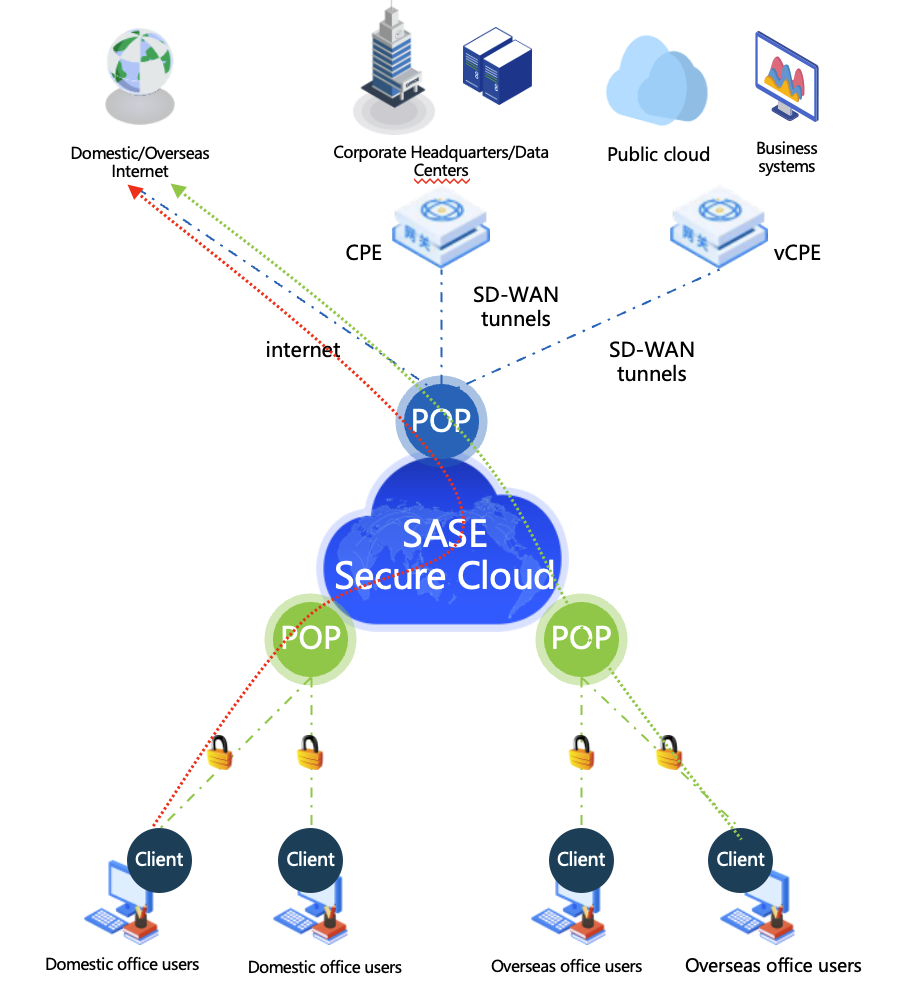
Flexible access to the Internet with zero exposure
• Zero trust access for users, supporting AD/LDAP, WeCom/DingTalk/Feishu
Converged, all-in-one security
• Integrate security capabilities such as data leak prevention, threat detection, and desktop management.
• Online Security Audit Day, Online Security Control, and Visual Security Management.
Proximity Access and Global Roaming
• When a mobile user roams globally, the security policy is accompanied by the user’s identity.
Cross-border data compliance
• Cooperate with carriers to provide compliant cross-border private lines.
SASE: Domestic Application Access Acceleration
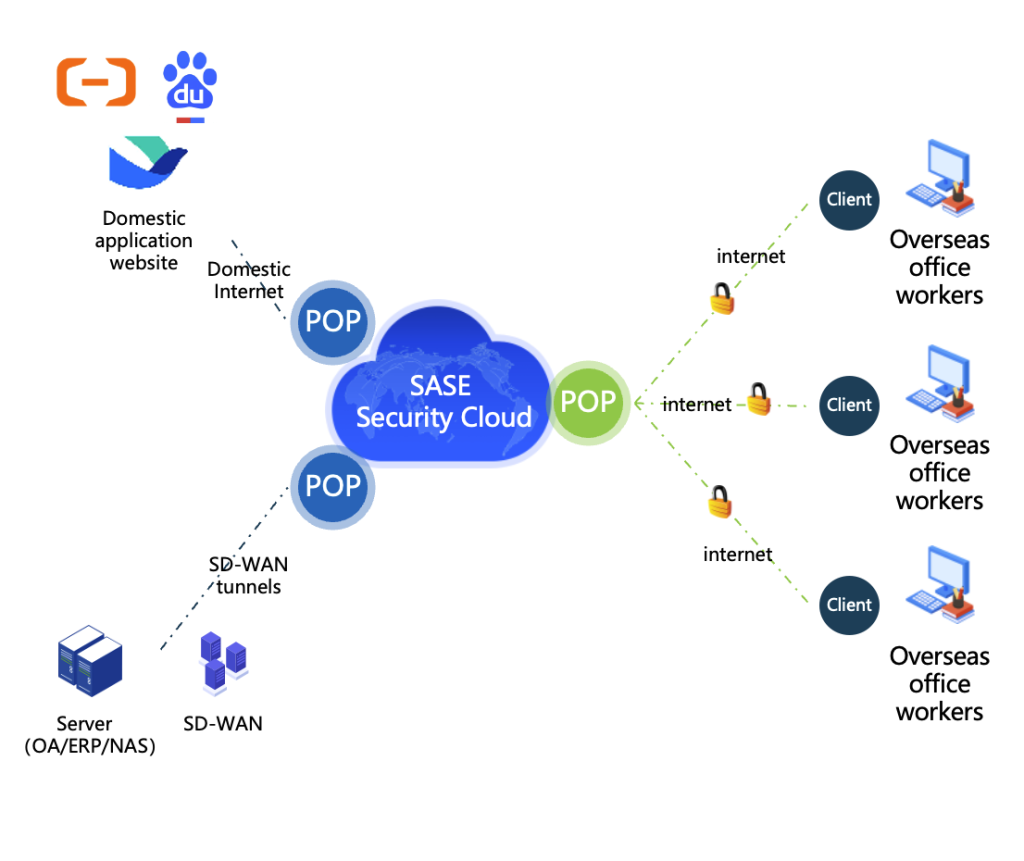
Asset-light
• On-demand subscription to security services greatly reduces security investment costs
Deploy quickly
Simplified O&M
• Online services are the mainstay, and the response to problems is more timely and faster
Easy to manage
SASE XDLP
solves the problem of traditional data leakage prevention products
Innovative technology is safe and trustworthy
Innovative monitoring mode
In terms of monitoring mode, the original monitoring outward tracking has been changed to full-link tracing from data download to outgoing
Data Recognition Optimization
In terms of data recognition, in addition to traditional regular expressions and machine learning, business contexts have been added, such as source applications, file lineage and other identification technologies
Improved risk assessment
In terms of risk assessment, global risk assessment is carried out using DLP, terminal DLP, network DLP, and UEBA technologies in all scenarios
Successful case
a new energy vehicle manufacturer
Customer pain points
1. The VPN performance of the traditional solution cannot support remote office requirements, and the bastion host is exposed to the outside world,resulting in a high risk of being attacked.
2. It is impossible to manage the equipment outside the company’s network, and the computers used by employees and the software installed are not clear.
3. Remote work cannot distinguish between employee devices, and the risk of leakage of sensitive design documents is high.
4. The office security protection capability is weak and cannot be linked with the network policy.
Customer benefits
1. The zero-trust access mode replaces VPN to meet the needs of remote office access.
2. Comprehensive IT asset management and control to realize the full-cycle management of enterprise application software.
3. Combined with the integration of user abnormal behavior analysis, sensitive data identification, and outgoing full-channel management and control capabilities, it reduces the risk of sensitive data leakage.
4. Terminal security is integrated, and access policies are linked to device security status.
A large manufacturing enterprise
Customer pain points
1. The safety level of the headquarters and branches (bases) is inconsistent, and the security risk of each branch visiting the headquarters is high
2. The demand for remote office is large, and the risk of data security is high
3. The scale of enterprise personnel is large, the terminal equipment is varied, and the control is difficult
4. The self-implementation of the zero trust system requires many application transformations and is difficult to implement.
Customer benefits
1. The hybrid deployment architecture implements one global network and achieves a consistent high security level in all scenarios
2. It integrates zero trust secure access and terminal device management, occupies less resources for lightweight operation, and improves the office experience of employees
3. Zero trust access mode helps enterprises work securely anytime, anywhere
4. The zero trust client is lightweight, and the zero trust security architecture is quickly implemented
Download Useful Resources
OUR VALUE
PROMISE
SIMPLIFY SD-WAN, SECURITY & MANAGEMENT
FOR AN GOIP AND CONNECTED NETWORK.
Maximise Business Benefits With
AGILE SECURITY AND NETWORK SOLUTIONS
FOR HYBRID WORK
Hybrid working, mobility and cloud adoption have disrupted traditional perimeter-based security. Enterprises need to adapt by bringing security controls closer to the edge and consolidating security and network functions in an efficient as-a-service model.
Our Managed SASE Solutions are integrated network and security offerings designed, delivered and managed by our experts. Its unified management platform provides you with context-led insights and proactive threat detection.
Did you know
Our IP backbone is ranked #1 worldwide?
OUR
CERTIFICATION

Penetration Testing Service Licence & Managed Security Operations Centre (SOC) Monitoring Service Licence 
Singapore SBO IMDA 
HK SBO OFCA 
ISO 27001 
ASP(MCMC) 
FCC 214 & FCC 499
CCIE
Cisco Certified Internetwork Expert
CISSP
Certified Information System Security Professional
LPIC
Linux Network Professional Certification
MCSE
Microsoft Certified Solution Expert
PMP
Project Management Professional
HCNA HCNA – R&S HCNA – STORAGE
Huawei Certified Network Associate
ACP
Alibaba Cloud Certified Professional
ACA
Alibaba Cloud Certified Associate
AWS ASSOCIATES
Certified Solutions Architect

CONTACT OUR
SALES & SOLUTION EXPERTS
Entrusted ICT Partners Across Industries
CERTIFIED
CLOUD PARTNER


