SECURITY
OPERATIONS CENTER (SOC)
(
What is
a Security Operations Center?
Imagine a central command center for your organization’s security. That’s the Security Operation Center (SOC). It combines skilled analysts, advanced tools, and well-defined procedures to constantly monitor your defenses.
This vigilance helps prevent attacks, detect threats early on, analyze their nature, and swiftly respond to any security incidents. Ultimately, the SOC works tirelessly to improve your overall security posture.
The SOC acts as your security nerve center, constantly gathering data from every corner of your IT infrastructure – networks, devices, applications, and data storage – regardless of location. This comprehensive view is crucial in today’s complex threat landscape, as advanced attacks often rely on scattered clues.
GOIP Group SOC
GOIP Group keeps your company safe around the clock. Our team of cybersecurity professionals acts as your 24/7 security watchtower, leveraging advanced security monitoring to detect threats and a comprehensive incident response plan to ensure a swift and effective response, keeping your business secure.
To keep your business safe and running smoothly, so you can focus on what you do best.
What does a
SOC do?
A high-functioning Security Operations Center (SOC) acts as your organization’s 24/7 security war room. This elite team combines cutting-edge technology with deep security expertise to continuously monitor your entire network. This allows for real-time incident response, where threats are neutralized before they can cause damage.
The SOC also drives ongoing security improvements, proactively identifying and patching vulnerabilities to keep your defenses ahead of evolving threats. In short, a high-functioning SOC provides an impenetrable shield against cyberattacks, giving you peace of mind and allowing you to focus on your core business.
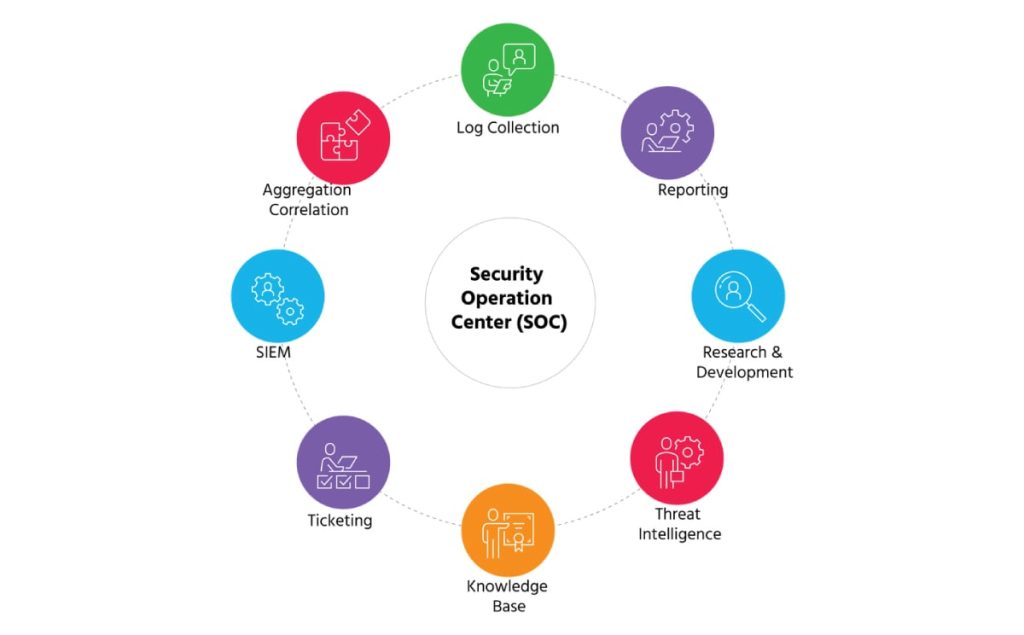
Who works in a SOC?
The SOC is staffed with highly skilled analysts and engineers, overseen by supervisors who keep the operation running seamlessly. These professionals are trained specifically to handle security threats.
They not only wield a wide arsenal of security tools but also possess the knowledge and procedures to swiftly respond and contain any security breach, ensuring your infrastructure remains secure.
The best SOCs leverage
The best SOCs leverage a team with a rich tapestry of skills and experience. This ensures they can effectively manage security challenges at every level.
These highly trained professionals work together seamlessly, constantly monitoring, analyzing, and responding to threats, keeping your organization safe from cyberattacks.
GOIP GROUP
SOLUTIONS
We offer flexible, managed and co-sourced Security Operations Center (SOC) services, partnering with boards and collaborating closely with your security team for a comprehensive defense against cyber threats.
Get a custom-fit security shield for your business. We offer flexible, on-site or remote SOC services tailored to your specific needs.
Security Operations Center (SOC) goes beyond geographical boundaries. Our “connected execution” approach leverages a team of cyber experts across APAC, including Hong Kong and Malaysia. This global network, combined with cutting-edge technology like cloud-native security analytics, automation, and threat intelligence, empowers us to deliver professional, location-independent security operations for your organization.
A global network of specialized cybersecurity teams unites to deliver world-class, custom-fit security solutions, ensuring consistent protection across regions with local support on-demand.
Our adaptable security solutions seamlessly adjust as your business expands. This allows you to transform your cyber operations, proactively reduce risk exposure, and focus on growth with complete confidence.
Our deep expertise in managed security services translates into actionable insights and recommendations, empowering you to make informed decisions about your organization’s security posture.
Our extensive experience translates into a proactive approach, leveraging lessons learned to identify and avoid potential security roadblocks for your organization.
Our deep understanding translates into relevant security insights and specialized advice on leading practices, keeping you ahead of industry-specific threats.
We combine onshore and offshore resources for optimal client coverage, ensuring knowledge transfer builds your team’s internal security capabilities.
Our innovative phase-driven structure maximizes efficiency with 24/7 coverage, surpassing the limitations of a traditional onshore-offshore model.
Our proven approach simplifies security: enhanced automation streamlines processes and delivers robust protection for your organization.
Our deployment accelerators minimize setup time, ensuring a smooth and rapid transition to a state of optimal security.
MANAGED
SERVICES
Backup
We offer flexible data recovery options, allowing you to restore individual files or entire systems based on your specific needs, all with customizable retention timeframes for complete peace of mind.
Compliance and Security
Our multi-layered security approach leverages cutting-edge technology to safeguard your data and streamline continuous compliance, ensuring peace of mind on both security and regulatory fronts.
Disaster Recovery
Real-time data replication and seamless failover between sites ensure your systems stay up and running, minimizing downtime and maximizing operational continuity.
Network Access
Our services accelerate application delivery while simultaneously fortifying your security posture, giving you the best of both worlds: faster deployments and robust protection.
Storage
We offer a flexible solution for both long-term archival and short-term data storage, maximizing value and streamlining your data management.
Edge
A fully managed platform delivering on-demand computing power exactly where you need it, for a seamless and scalable cloud-like experience at the edge.
What GOIP Group
can provide?
Stay ahead of cyber threats with industry-leading intelligence and a mature 24/7 SOC.
Our experts leverage cutting-edge knowledge to proactively hunt threats, engineer security content, and fuse threat data, delivering a comprehensive response system that keeps your organization secure.
Download Useful Resources
Did you know
Our IP backbone is ranked #1 worldwide?
OUR
CERTIFICATION

Penetration Testing Service Licence & Managed Security Operations Centre (SOC) Monitoring Service Licence 
Singapore SBO IMDA 
HK SBO OFCA 
ISO 27001 
ASP(MCMC) 
FCC 214 & FCC 499
Entrusted ICT Partners Across Industries
CCIE
Cisco Certified Internetwork Expert
CISSP
Certified Information System Security Professional
LPIC
Linux Network Professional Certification
MCSE
Microsoft Certified Solution Expert
PMP
Project Management Professional
HCNA HCNA – R&S HCNA – STORAGE
Huawei Certified Network Associate
ACP
Alibaba Cloud Certified Professional
ACA
Alibaba Cloud Certified Associate
AWS ASSOCIATES
Certified Solutions Architect

CONTACT OUR
SALES & SOLUTION EXPERTS
Entrusted ICT Partners Across Industries
CERTIFIED
CLOUD PARTNER




